
Ransomware Demystified
or
You are not serious about cybersecurity, and you got what was coming to you.
or
How to fool people and keep your job
Part One:
This is not an overly technical article. I believe that would be inappropriate as I want the reader to understand the current predicament in its most holistic way.
The past few months have been hectic and filled with an interesting parade of anomalies so it has been difficult to budget time appropriately so that my digital travels can be documented properly. For this I lament. It is due to this process of lamenting that I have been compelled to comment on what is in my opinion the continuous egregious portrayal of cybersecurity in the course of current events. I speak to you of course of ransomware and most recently the incidents involving the Baltimore and Washington DC Police Department as well as Colonial Pipeline.
Before we begin, for those who have never come across any of my rantings, it would be appropriate to provide some context. Usually, we take malware and provide an in-depth analysis. This diatribe is going to be a little different. The first part is simply a condemnation of society and all elements from within, which not only perpetrate the absurdity of what cybersecurity has become but continue to make people believe that it is acceptable. Remember these are the same people that claim there is a shortage of talent. What is discussed here must be said, albeit even one lone voice, perhaps if we scream loud enough, we can be heard. Following my ramblings there will be some technical observations and a discussion on the ransomware issue whose arthritic hand has gripped the fragile throat of the world.
The state of cybersecurity is abysmal and continues down that dysfunctional spiral which leads to the multiple circles of the inferno. Both corporate America and most governments have given their citizens the belief that this is okay and must be accepted. As a collective we are led to believe that “Big Tech” must not be trusted but everything else is okay. Facebook and Google are evil, but the courts sharing your information with third parties is acceptable. I must view Apple as demonic, but if an app loses my credentials and credit card information, I must look the other way. If my car is stolen, the police will tell me who stole it and where they found it. If an app that is storing all my information or an office loses my information all I am told is that there was a breach, I am told nothing of the breach, what happened and more importantly where did the information go. If I am lucky, I am told it is on the “dark web”, but I will not be told where. For that you need to look for someone like me to go look for it. That is absurd.
Recently one of my accounts fell victim to the Park Mobile app breach. Now despite what is said about Google, Apple, or Amazon, I would never give an app my credit card information. I link this to Apple pay, Google Pay, or Amazon where my account has two factor authentication using an authenticator app. If I was foolish enough to use an active email address with my credit card number I would be in a horrible situation because not only, do I have to worry about my card being used, but I also have to worry about identity theft on a more amplified level. It is advisable when setting up subscriptions online to use an email address for that purpose and use a payment provider such as PayPal, Apple Pay, Google Pay, or Amazon Pay. Do I trust those providers, most definitely not, but I know the one thing I can do is have one central area to control those subscriptions and if something is not right I will not have to call the bank for a new card.
As an individual you can navigate around Google, Apple, and Amazon and control the narrative as you can make them accountable to you, you just have to know how.
What you cannot make accountable is a governmental institution, or a corporation that is protected when they lose your personal and financial data. Worse it seems that many states can just give it to third parties upon request. I am not afraid of Google, Amazon, or Apple because I can control the narrative and so can you. What bothers me is something like the following:
- A dental office allows my patient data including payment information to be compromised and the only thing I am told is that its out there, but we will give you free credit monitoring for six months.
- Many moons ago when I went to the courthouse with my wife to get our marriage license, we viewed this as a happy day. After the marriage we received correspondence from two attorneys stating that it’s important to make sure that our immigration status is kept up to date and they can represent us because failure to do so would result in deportation. This is amusing as I am a citizen of the United States who was born here, and my wife is a naturalized citizen. Apparently as our names would be deemed ethnic the data was shared, there was no permissions prompt for me to click “you can share this.”
- An app used for parking suffers a breach and does not tell you it has nor does it offer guidance. Username, car information, credit card information is all compromised, and it does not seem to bother them.
I can go on, but I trust that you get the point, which now brings us to the issue of ransomware. We will dismiss from the standard introduction by defining what ransomware is, if you are here, you already know. However, if you are not one whose face and soul is filthy from the dirt in the proverbial cyber trenches, what you may not know is that ransomware is not the threat it is made out to be and is completely avoidable. In fact, Trojans are more of a threat than ransomware.
The common consensus to the statement of ransomware being completely avoidable is that this cannot be true because if police and large corporations can be tricked, this means the trickster must be some evil genius and there is nothing anyone can do. Well, this is not only foolish but ridiculous. Further, if you accept this statement that means you also believe that those who maintain the infrastructure could have never seen this coming. There is an analogy I like to use. If you hire a plumber, and that plumber floods your house through incompetence, chances are that plumber will have a hard time finding work. Two professions I know this truth does not hold, lawyers and high-level corporate cybersecurity.
There is no genius in ransomware, there is no grand plan. So how did this happen? It is politically incorrect to say but we are going to say it anyway. They were stupid and lax. In fact, Colonial lost 100 gigs of data before the main attack within two hours. How no one saw that is mind numbing. The Baltimore PD does not like keeping their infrastructure up to date but will have no problem hauling you in for the most minute offense. This is unacceptable.
When guarding your infrastructure, the following things need to be adhered to, there is no deviation from this – it simply must be followed:
- Do not treat cybersecurity as an after-thought. Data is currency. Start taking things seriously.
- All computers including air-gapped computers must be patched and updated, including virus signatures. If they are air gapped, you must schedule the time for upgrades and do so manually only using updates downloaded from the operating system repository and they must be checked. If your computers are networked your life is easier because you can enable auto updates. Your browser needs to be updated as well.
- Two levels of malware protection are needed. Windows Defender is fine for a base but add on top of this Malwarebytes for Business or whatever package you may prefer so long as you keep the program updated.
- Limit admin rights to a workstation, people should not be logging into workgroups, each workstation should be set with appropriate permissions and your users should not have broad permissions.
- Make sure that your SIEM or Intrusion detection system is up to date. If you do not know what that means email me and I will tell you because if you are a business, you need to get one.
- If you are a Microsoft 365 shop, make sure you are using OneDrive Ransomware protection. Also Azure Sentinel can be setup for a retention time of 7 days and it is free. Use it, while you’re at it make sure if you have an E5 license and you are watching what goes on in Microsoft 365 Security and Compliance.
- Watch your backups like you watch your bank account, make sure they are safe and test them.
- Setup alerts, your business follows a set of prescribed norms, your alerts will show you if someone is deviating.
- If you’re going to decide to run your own mail server because you do not trust hosted providers, then you must accept the responsibility that comes with that.
- Start logging DNS activity. Security Onion is free, and storage is cheap. For large corps if they were logging DNS they would have caught SolarWinds. There is no excuse.
- If your running critical systems, only install on the computer what you need, in fact if you’re in the corporate space, you should only have what you need on the computer.
These are the pillars of good security, it is not hard, it simply requires diligence and a level of discipline and a dismissal of the dysfunctional conventions that you are told that you need to practice.
The problem that we encounter, and it is mind numbing that this occurs, corporations and the very people who are placed there to guard the infrastructure have no type of practical knowledge or understanding of application. They simply follow the same tired playbook to its absurd psychotic conclusion. Why? There is no accountability and data is not viewed in the same currency as a physical asset, yet it ends up being treated that way when the ransom has to be paid or someone stole your information. Until the mindset changes then this will happen again and again – cybersecurity is truly in a sorry state.
Now that you the reader understand the calamity of what is involved, it is important we go over some basic tenants of what ransomware does. It's not too technical so just follow me.
Part Two:
For our analysis we looked at two variants. Babuk and Crysis, and for Babuk, delving deeper we look at the code in Ghidra. I use any.run for volatile malware testing. I deem anything volatile that I have a high belief that if it gets out that it will be highly problematic to recover from the disaster. While I have no respect for ransomware developers, I respect the potency of the carnage it causes. The malware will not just run on the machine, once it finishes enumerating all processes and encrypting documents, it will move onto the network, if you have a Windows network with any open shares (way too many people do) then it will hit those shares and other machines. Hence, I prefer a more controlled venue for my ransomware testing and any.run serves this purpose very well.
It is important to remember that with any malware, there is no secret weapon, like any malicious entity, they have to get in first, and for the most part with some very rare exceptions you (the user) have to click or agree to something. That will always be the first event because an action needs to occur before the malware is activated. If you do not click, if you do not activate the malware, its not going to run. (for the most part).
Remember, ransomware encrypts all your files, how does it do that? When the malware is activated, it needs to find the files, it must run a program to do this. For this purpose, on a Windows computer, the Volume Shadow Services is activated, and a process called enumeration begins.
The Volume Shadow Services will almost always start from the command line after the malware has been activated:
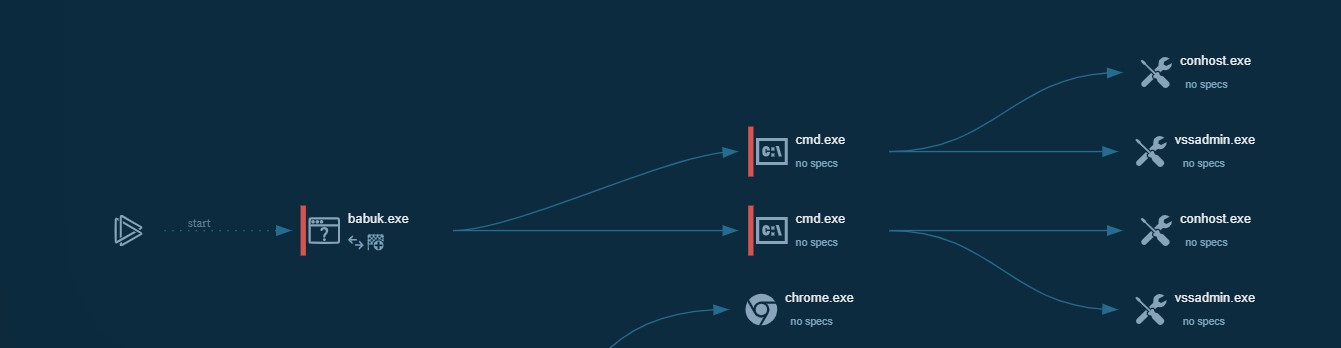
Now keep in mind, you will not see the Volume Shadow Services load, a command shell which is not viewed by the user is launched:
"C:\Windows\System32\cmd.exe" /c vssadmin.exe delete shadows /all /quiet
The Volume Shadow Services allows backup applications to back up locked and open files. Both the backup application and software application must be VSS-aware to utilize VSS to back up open or locked files, that would include all documents stored on your computer. That command is deleting all backup copies that Windows stores on your computer.
For the Babuk strain of ransomware, the developers are very brazen. Most of the time malware authors will obfuscate their code to prevent revere-engineering. This is not the case as noted below:
